UK Cybersecurity in 2025: How Operational Disruption Became the New Attack Strategy
Case Studies
2025 marked a turning point for UK cybersecurity.
Cyber attacks across the UK increasingly moved beyond isolated data breaches and became full-scale operational disruptions — shutting down services, halting supply chains, and forcing organisations into prolonged recovery modes.
According to the UK National Cyber Security Centre (NCSC), the number of “nationally significant” cyber incidents responded to over the past year more than doubled compared with the prior period, underscoring escalating threat complexity and impact.
Key Takeaways for UK CISOs and Security Leaders
- Operational disruption is now the goal: Many of the most damaging incidents targeted service availability rather than merely data theft.
- Supply chain risk became first-party risk: Attacks on healthcare and retail suppliers showed how third-party compromise can directly halt core operations.
- Automation shifted the balance: Attackers increasingly use tooling to probe APIs, workflows, and logic paths faster than human teams can triage.
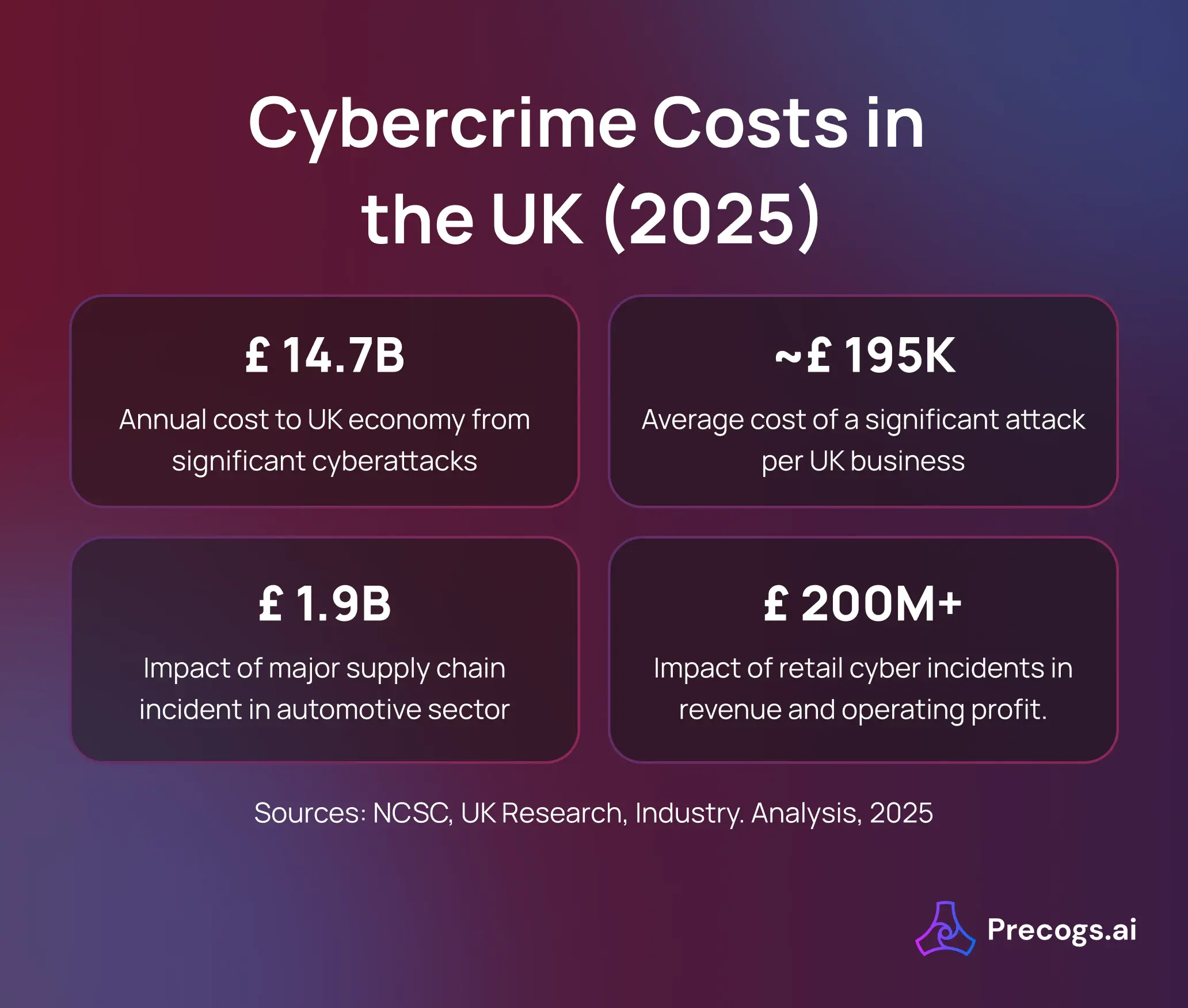
- Cybercrime’s economic toll is substantial: Independent UK research places the annual cost of significant cyber attacks to the UK economy at an estimated £14.7 billion, equivalent to around 0.5% of GDP. The average cost of a significant attack to a UK business is approximately £195,000.
- Speed is the differentiator: Organisations that reduced time-to-fix reachable vulnerabilities contained impact more effectively.
- The direction of travel is clear: UK security teams are moving toward AI-assisted, logic-aware defense to reduce exploitable paths earlier.
Cyberattack Costs in Context
The economic impact of cyber attacks in the UK is significant and multifaceted:
- Government-commissioned research estimates the average cost of a significant successful cyber attack for a UK business at nearly £195,000, scaled to an estimated £14.7 billion per year across the UK economy — roughly 0.5% of GDP. GOV.UK
- In addition to the broad national cost, individual large-scale incidents have inflicted hundreds of millions to billions of pounds in damage. For example, independent analysis of a major automotive supply chain incident in 2025 suggested the economic impact could be as high as £1.9 billion to the broader UK economy, factoring in output losses across suppliers and production delays. The Guardian
- Retail sector breaches reported in 2025 caused tens to hundreds of millions of pounds in losses for affected companies, with one major UK retailer reporting an £80 million operating profit hit and over £200 million in lost revenue in the first half of the year following a disruptive incident. Reuters
These figures reflect direct costs (lost revenue, operational disruption) as well as indirect costs (recovery, remediation, customer impact), and indicate that cost profiles vary substantially by size, sector, and incident type.
Major UK Cyber Incidents in 2025
Across publicly disclosed incidents and representative industry case studies, several consistent patterns emerged:
- Large UK enterprises experienced system shutdowns that rippled across manufacturing, logistics, and customer-facing services.
- Major high street retailers faced payment, fulfilment, and availability disruptions that dented revenue and operational performance.
- Local authorities and public sector bodies dealt with unauthorised access to sensitive systems, often involving legacy infrastructure.
- Healthcare and NHS suppliers were targeted as indirect entry points, amplifying downstream disruption to patient services.
These incidents differed in sector and technique but shared one outcome: business interruption at scale.
The emerging “AI vs AI” reality
While not every incident can be attributed to artificial intelligence, the broader trend of automation and rapid iteration is unmistakable.
Modern attack operations increasingly rely on automation to:
- Scale credential abuse and access attempts.
- Probe APIs and control planes rapidly.
- Generate high-variation payloads to evade static detection.
- Execute fast feedback loops against defensive controls.
This creates an “AI vs AI” dynamic — attackers compress their attack cycles, while defenders must compress detection, prioritisation, and remediation cycles to match. Traditional security models struggle under this pressure.
Why Traditional Defenses Fell Behind
Across incidents, the same defensive gaps repeatedly appeared:
- Slow remediation of known, reachable vulnerabilities
- Alert overload without exploitability prioritisation
- Fail-open behaviour when security systems degraded under load
- Limited visibility into how individual issues chain into real impact
Finding vulnerabilities is no longer sufficient. Closing them fast enough is the real challenge.
The Shift to AI-Speed Defense
The lesson from 2025 is not that organisations need more tools, but that they need faster, smarter security loops.
Defence now requires:
- Understanding how attackers chain logic, not just where bugs exist
- Prioritising reachable high-impact issues
- Integrating remediation directly into development workflows
This is the problem space Precogs AI is built for. Rather than treating vulnerabilities as isolated findings, Precogs focuses on reducing exploitable paths by combining logic-aware analysis, reachability-based prioritisation, and PR-ready remediation. The goal is simple: shorten the gap between exposure and fix before attackers can weaponise it.
Looking Ahead: Priorities for 2026
- Hardening control planes, such as token systems and authorization logic
- Supplier security enforcement and incident-ready SLAs.
- Fail-safe architectures for critical gates.
- Continuous exposure testing (DAST on APIs and key workflows).
- Compressed remediation loops with automated prioritisation.
2025 showed that the cost of cyber attacks is not just monetary; it’s operational, strategic, and reputational. In 2026, defence must be as rapid and adaptive as attack.
Explore the Cybersecurity 2025 Series
1. Global Cybersecurity 2025: The Year Code Broke the Physical World
2. US Cybersecurity 2025: When Software Failure Became a National Disruption
3. EU Cybersecurity 2025: When Regulation Met Reality
4. MEA Cybersecurity 2025: Digital Transformation Under Fires
5. APAC Cybersecurity 2025: When Supply Chains Became the Front Line
Sources & References
- UK National Cyber Security Centre (NCSC) — Annual Review 2024–2025
- Cyber Security Breaches Survey 2025 (UK Government)
- UK Supply Chain Cyber Attack Economic Impact Analysis (The Guardian, 2025)
- Financial Impact of UK Retail Cyber Incidents (Reuters, 2025)
- Industry Research on Automated and AI-Driven Cyber Attacks (2024–2025)
