Global Cybersecurity 2025: The Year Code Broke the Physical World
Case Studies
2025 will be remembered as the year cyber attacks stopped being abstract IT failures and became physical, economic, and societal disruptions.
Factories halted production. Hospitals cancelled procedures. Global supply chains stalled. In every case, the root cause was the same: software logic was reached, trusted, and abused at machine speed.
From manufacturing giants like Jaguar Land Rover and Asahi Group, to healthcare providers affected by the Change Healthcare ransomware attack, to enterprise platforms impacted by OAuth and identity abuse, the most costly incidents of 2025 demonstrated a new reality:
If your business runs on code, your business is directly attackable — in real time.
This global year-end review examines the most serious and costly cyber incidents of 2025, the patterns that connected them, and why 2026 will be defined by AI-speed logic warfare.
Key Global Takeaways for CISOs and Security Leaders
- Cyber attacks became kinetic: Software failures triggered real-world shutdowns across manufacturing, healthcare, and logistics.
- Identity replaced the perimeter: OAuth tokens, service accounts, and API trust relationships were repeatedly abused.
- Zero-day velocity collapsed response windows: The time between vulnerability discovery and mass exploitation shrank to hours.
- Logic beats malware: Attackers increasingly bypassed controls without “breaking in.”
- The economic impact is massive: Individual incidents caused losses ranging from hundreds of millions to multiple billions of dollars.
- Speed is survival: Organizations that closed exploitable paths fastest limited damage.
The 2025 Global Crisis Map: Incidents That Defined the Year
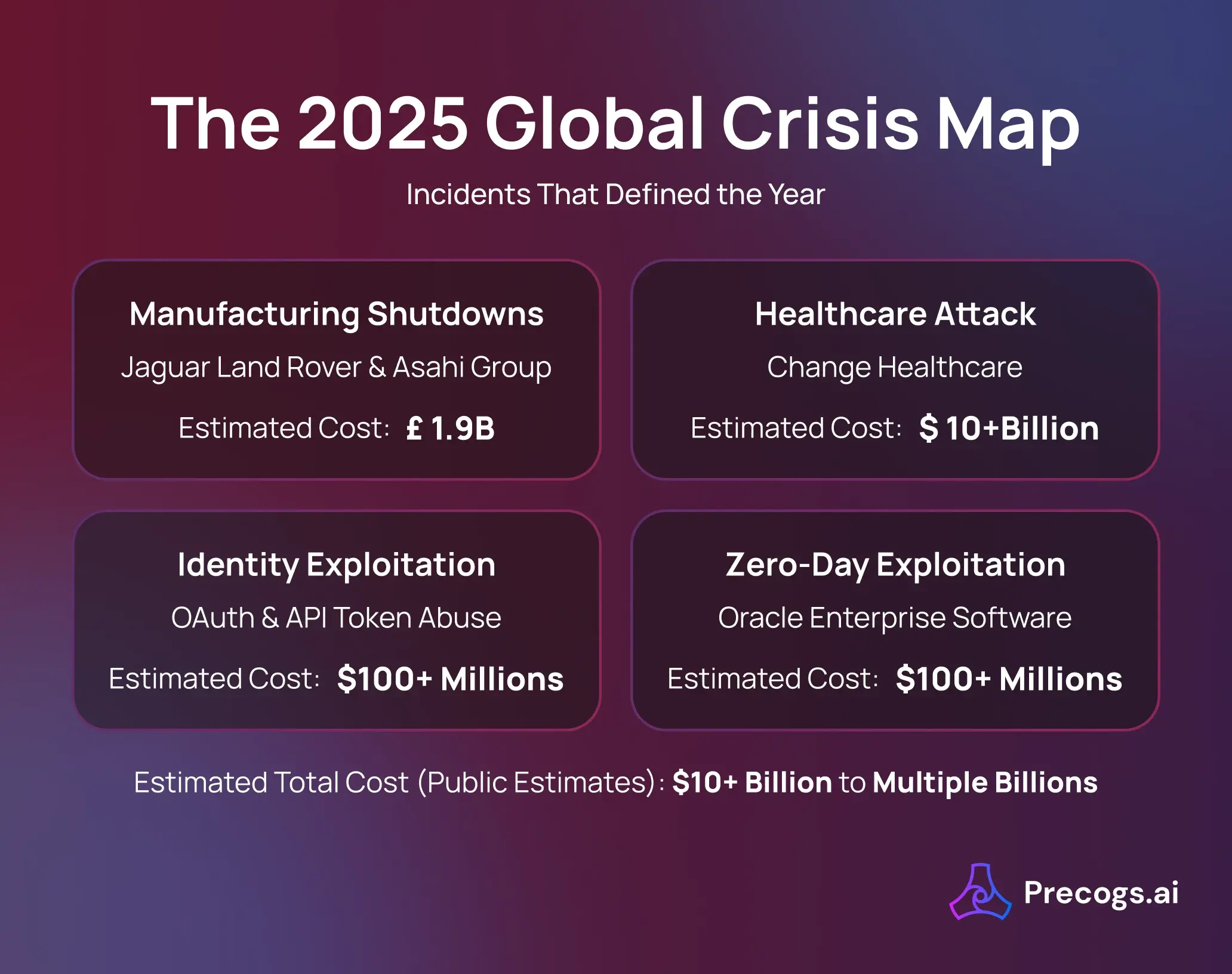
1. Manufacturing Shutdowns: Jaguar Land Rover & Asahi Group
Sector: Automotive & Industrial Manufacturing
What happened
In 2025, cyber incidents forced production halts at major manufacturers, including Jaguar Land Rover (UK) and Asahi Group (Japan). Public disclosures and reporting confirmed that attackers reached systems critical to manufacturing operations, triggering controlled shutdowns to prevent further damage.
Estimated cost
- Independent economic analysis estimated the Jaguar Land Rover incident alone had a downstream impact of approximately £1.9 billion on the UK economy when supplier and production losses were included.
- Asahi Group reported significant operational disruption across breweries, with losses estimated in the hundreds of millions of dollars, factoring halted production, recovery costs, and supply delays.
Why it matters
Operational Technology (OT) became a primary hostage. These incidents proved that cyber attacks no longer need ransomware or data theft to be devastating — stopping production is enough.
2. Healthcare at Scale: Change Healthcare
Sector: Healthcare & Insurance (United States, Global Impact)
What happened
The ransomware attack on Change Healthcare, a critical US healthcare payment processor, continued to reverberate through 2025. The attack disrupted prescription processing, claims management, and patient services across thousands of hospitals and pharmacies.
Estimated cost
- UnitedHealth Group disclosed over $2.8 billion in direct costs related to response, recovery, and business disruption.
- Industry analysts estimate broader economic and healthcare system impacts exceeded $10 billion, including delayed care and operational downtime.
Why it matters
This incident demonstrated how single points of failure in healthcare supply chains can cascade into national-scale service disruption, even without direct attacks on hospitals themselves.
3. Identity Exploitation: OAuth Abuse Across Enterprise SaaS
Sector: Enterprise Software / SaaS
What happened
Rather than breaching core platforms directly, attackers exploited OAuth tokens and third-party integrations to gain persistent, legitimate-looking access to enterprise SaaS environments, including CRM and financial systems.
High-profile investigations revealed that attackers did not “hack” platforms like Salesforce — they abused delegated trust designed into modern SaaS ecosystems.
Estimated cost
- Losses were often under-reported, but analysts estimate hundreds of millions of dollars globally in data exposure, incident response, regulatory risk, and customer churn.
- Many organizations experienced months of silent data exfiltration before detection.
Why it matters
Identity is now the perimeter. APIs and tokens became high-value attack surfaces, often monitored less rigorously than traditional authentication flows.
4. The Zero-Day Blitz: Oracle Enterprise Software
Sector: Enterprise Infrastructure
What happened
A critical zero-day vulnerability in Oracle enterprise software was exploited at global scale before organizations could patch. Attackers moved from discovery to mass exploitation in a matter of hours.
Estimated cost
- While Oracle did not publish aggregate loss figures, industry estimates place global remediation and disruption costs in the high hundreds of millions of dollars, driven by emergency patching, forensic response, and system downtime.
Why it matters
The traditional patch-management model failed. When exploitation velocity exceeds organizational change velocity, being “aware” of a vulnerability is meaningless.
The Defining Pattern of 2025: Logic Warfare
Across all major incidents, a single pattern emerged: attackers focused on business logic, not brute force.
- They didn’t crack encryption — they found the API call that bypassed controls.
- They didn’t guess passwords — they reused tokens with unintended privilege.
- They didn’t flood networks — they navigated workflows exactly as designed.
AI-assisted tooling enabled attackers to:
- Continuously probe APIs and workflows
- Map authorization paths automatically
- Chain small logic flaws into major impact
- Adapt instantly to defensive changes
This was logic warfare, executed at machine speed.
Why Traditional Security Failed
Despite billions spent on security tooling, many organizations shared the same weaknesses:
- Scanners that detect syntax, not intent
- Alert overload without exploitability context
- Remediation cycles measured in weeks
- Controls that failed open under pressure
- No visibility into reachable attack paths
Finding vulnerabilities was not the problem. Closing them before exploitation was.
The 2026 Mandate: AI-Speed Defense
The lesson from 2025 is unambiguous:
If an AI-assisted attacker can find and exploit a logic flaw instantly, defense must operate at the same speed.
The Shift to AI-Speed Defense with Precogs AI
Precogs AI is designed for this reality.
Rather than producing more alerts, Precogs focuses on reducing exploitable paths by:
- Reasoning over code and dependencies to understand intent
- Identifying logic and authorization flaws attackers actually use
- Prioritizing issues by reachability and real-world impact
- Generating PR-ready remediation to close gaps immediately
In an era of logic warfare, defense must think like the attacker — and move faster.
Looking Ahead
2025 proved that cyber risk is no longer theoretical.It is operational, financial, and physical.
2026 will belong to organizations that:
- Treat identity and APIs as critical infrastructure
- Close logic gaps early
- Compress remediation cycles to machine speed
The world changed.
The only question is whether your security model did.
Sources & References
The analysis and cost estimates in this report are based on publicly available disclosures, regulatory filings, government statements, and investigative reporting from the following sources:
Jaguar Land Rover cyber incident and economic impact
- UK media and economic analysis reporting on production disruption and downstream supply-chain impact, including estimates of approximately £1.9bn in economic cost.
- The Guardian, “Jaguar Land Rover cyber incident cost UK economy billions” (2025).
- UK industry and manufacturing impact assessments.
Asahi Group production disruption
- Public statements and reporting on operational shutdowns affecting brewing and logistics operations following a cyber incident.
- Nikkei Asia, Reuters coverage of manufacturing disruption in Japan (2025).
Change Healthcare ransomware attack
- UnitedHealth Group public disclosures and SEC filings confirming over $2.8bn in direct costs.
- U.S. Department of Health and Human Services (HHS) statements and industry impact analysis.
- Reuters, “UnitedHealth details costs and disruption from Change Healthcare cyberattack” (2024–2025).
Enterprise SaaS OAuth and identity abuse
- Investigative reporting on large-scale OAuth token abuse impacting enterprise SaaS environments.
- Security research publications and incident response firm briefings on identity-based attacks.
- Reuters and cybersecurity industry analysis on third-party app exploitation.
Oracle enterprise software zero-day exploitation
- Security advisories, CVE disclosures, and global incident response reporting related to Oracle enterprise software vulnerabilities.
- Reuters and industry analyst commentary on rapid exploitation timelines and remediation costs.
Global and UK cyber incident trends
- UK National Cyber Security Centre (NCSC), annual incident management reporting.
- Government-commissioned research on the economic impact of cyber attacks on the UK economy.
- World Economic Forum (WEF) Global Cybersecurity Outlook (2025).
Explore the Cybersecurity 2025 Series
1. US Cybersecurity 2025: When Software Failure Became a National Disruption
2. UK Cybersecurity in 2025: How Operational Disruption Became the New Attack Strategy
3. EU Cybersecurity 2025: When Regulation Met Reality
4. MEA Cybersecurity 2025: Digital Transformation Under Fires
5. APAC Cybersecurity 2025: When Supply Chains Became the Front Line
Disclosure
This report combines confirmed public incidents with representative industry analysis based on widely reported patterns observed in 2024–2025. Cost figures are estimates derived from public disclosures and independent economic analysis and should be interpreted as indicative rather than definitive.
